81 | Add to Reading ListSource URL: www.cis.syr.eduLanguage: English - Date: 2005-04-21 18:24:41
|
|---|
82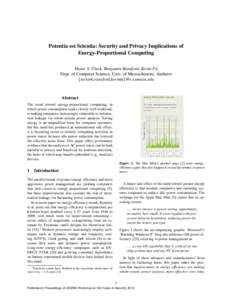 | Add to Reading ListSource URL: sharps.orgLanguage: English - Date: 2013-02-04 13:02:13
|
|---|
83 | Add to Reading ListSource URL: www.cs.virginia.eduLanguage: English - Date: 1999-09-01 15:39:58
|
|---|
84 | Add to Reading ListSource URL: faculty.nps.eduLanguage: English - Date: 2008-05-06 17:12:31
|
|---|
85 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2010-03-21 15:11:32
|
|---|
86 | Add to Reading ListSource URL: www.volkerroth.comLanguage: English - Date: 2007-11-23 00:00:08
|
|---|
87 | Add to Reading ListSource URL: courses.engr.illinois.eduLanguage: English - Date: 2015-04-20 13:04:03
|
|---|
88 | Add to Reading ListSource URL: www.ieee-security.orgLanguage: English - Date: 2017-04-03 15:58:27
|
|---|
89 | Add to Reading ListSource URL: joye.site88.netLanguage: English - Date: 2018-07-11 18:14:38
|
|---|
90 | Add to Reading ListSource URL: jjcweb.jjay.cuny.eduLanguage: English - Date: 2017-03-25 12:07:19
|
|---|